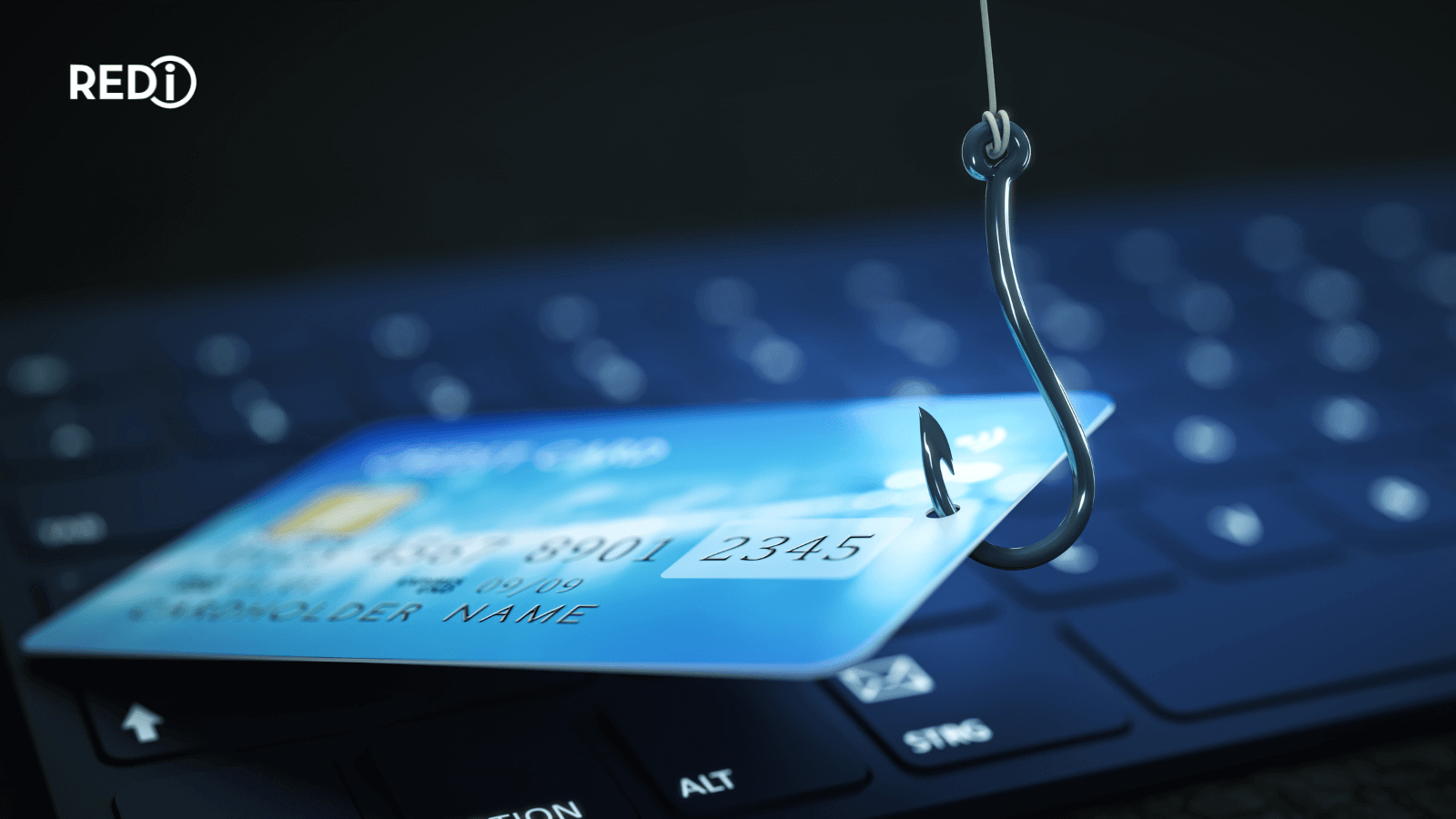
What is a BIN Attack?
The theft of a Bank Identity Number (BIN), which is the first six digits of a credit or debit card number, is at the center of a BIN attack. These details are used by hackers to generate fresh card numbers and conduct fraudulent transactions. BIN attacks can be conducted using a variety of techniques, such as malware, phishing schemes, and the sale of BINs obtained illegally on the dark web.
In a BIN attack, scammers use the Bank Identification Number (BIN), which makes up the first six digits of a credit or debit card account number, as the starting point for “guessing” the remaining ten digits.
Fraudsters use software to generate thousands of potentially valid card numbers, then test those numbers by attempting small transactions at various online retailers. When a transaction is approved, the perpetrators have a usable card number with which they can perpetrate fraudulent transactions and use them to discover more valid account numbers.
BIN attacks fall into two broad categories of fraud, CNP (card not present) fraud, because there is no physical card involved, and brute force attacks, which are characterized by a high number of automated attempts to gain unauthorized access to accounts.
Community Banks and Credit Unions: More Vulnerable Than Ever
While community banks and credit unions have the same imperative as larger financial institutions to protect their customers, members, and their own interests, they tend to be easier targets for BIN attacks because they often lack the human and technology resources of their bigger counterparts. The effects of a BIN attack on small banks and credit unions can be catastrophic, leading to large financial losses and harm to their reputation. When a successful BIN attack has been perpetrated, customers and members are, at best, inconvenienced and at worst doubtful that the institution has the capacity to safeguard their accounts.
Preventing and Mitigating the Impact of BIN Attacks
The first step to preventing and mitigating BIN attacks is to know what to look for. Because BIN attack scammers use targeted small transactions, they can be hard to spot, but there are red flags that may signal a BIN attack in progress. These include:
- A high number of small transactions originating from the same IP address.
- A high number of declines
- Odd transaction times
- Transactions originating overseas without prior travel notification on
- Any other activity that is unusual for your customers and members
- Increase in declines for invalid CVV or expiration date
Step two is to engage a third-party fraud prevention partner and implement digital fraud detection tools to analyze and detect fraudulent transactions quickly before BIN attacks get too out of hand.
And finally, all financial institutions should have a clearly defined response strategy in place in the case of a BIN attack. This strategy should include rapid containment of the attack, customer notification, and collaboration with law enforcement and other institutions.
It is vital for community banks and credit unions to remain vigilant and proactive in their security measures, given the evolving nature of cyber threats. Furthermore, institutions must conduct regular assessments of their security protocols to identify vulnerabilities and make necessary improvements to thwart potential attacks.
Bottom Line
BIN attacks pose a serious threat to the financial stability of community banks and credit unions. As the digital world evolves, financial institutions must take proactive measures to prevent and mitigate the impact of these attacks. By staying vigilant, working together, enlisting the help of fraud experts, and implementing the right technologies ac financial institutions can protect themselves and their customers from the devastating effects of BIN attacks.
Download the BIN Attack Playbook for Community Banks and Credit Unions Here